Deploy Zscaler Client Connector to macOS with Intune

This is the second of four posts where I will describe how to deploy Zscaler Client Connector (aka the app) to the different OS platforms Zscaler and Intune support. The goal is to deploy the app and prepopulate all required information to the app to create as little user friction as possible. I continue with macOS. This is what it will look like.

Well that was silent wasn’t it? So let’s see how to deploy Zscaler with Intune - without notarization or an Apple Developer Account.
To achieve this, we need to configure a few things
- Push Zscaler Root Certificate to device
- Build installation script
- Deploy script through Intune
- Enable Microsoft Enterprise SSO plugin
How To
First of all create a user group that
- is assigned to ZIA / ZPA enterprise applications in Azure AD
- has an Intune license
- can install the company portal on macOS and enroll their device You may already have that.
Push Zscaler Root Certificate to device
If your using SSL Inspection (which I recommend) you may have noticed that you can install the Zscaler Root CA Certificate through the App Profile in Zscaler Mobile Portal. Yes, there is a switch, but no. Because the certificate will not be trusted if it’s installed by the Zsaler installer
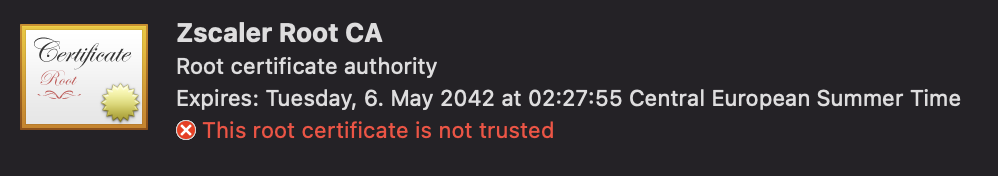
SSL Inspection will fail with error.

So we need to deploy that through Intune.
First we need to download the Zscaler Root Certificate from ZIA Portal. Go to Policy > SSL Inspection > Advanced SSL Inspection Settings and download the Zscaler Certificates. Unzip the file.

Create a configuration profile in Intune to push the certificat to the device. Go to Devices > macOS > Configuration Profiles > + Create Profile > Select Profile Type: Template > Trusted Certificate.
 Upload the previously downloaded certificate. Assign the profile to the user group!
Upload the previously downloaded certificate. Assign the profile to the user group!
Build installation script
We will use a script to deploy Zscaler. You can find it on my GitHub or below. It is based on a post on emm.how by user daniil_michine. I modified it to enable Single Sign on and disable autoupdate.
|
|
What does this script do?
- Download the app from Zscaler
- Do fancy stuff like wait for curl
- Install Zscaler with arguments
You only need to modify lines 15-17 to customize it for your environment
|
|
| Setting | Value |
|---|---|
cloudName |
The name of you ZIA cloud without tld. zscaler.net = zscaler zscloud.net = zscloud |
userDomain |
Domain name you use for authentication. Different UPN suffixes require different VPN Scripts. |
webUrl |
Path to your Installation Zip file |
The webUrlcan be copied from the Zscaler Mobile portal because the Zscaler installer is more or less publicly available.

The variable autoUpdate="true" tells the script that Zscaler handles application updates. If a version of Zscaler Client Connector is already installed, it won’t reinstall.
Troubleshooting
You may want to test the script locally before uploading it to Intune.
- Save the script to folder
- Open Terminal, go to folder
- Run
sudo chmod u+x yourScript.shto make the script executable - Run
sudo sh yourScript.shif it’s successful Zscaler will open in the tray
Deploy script through Intune
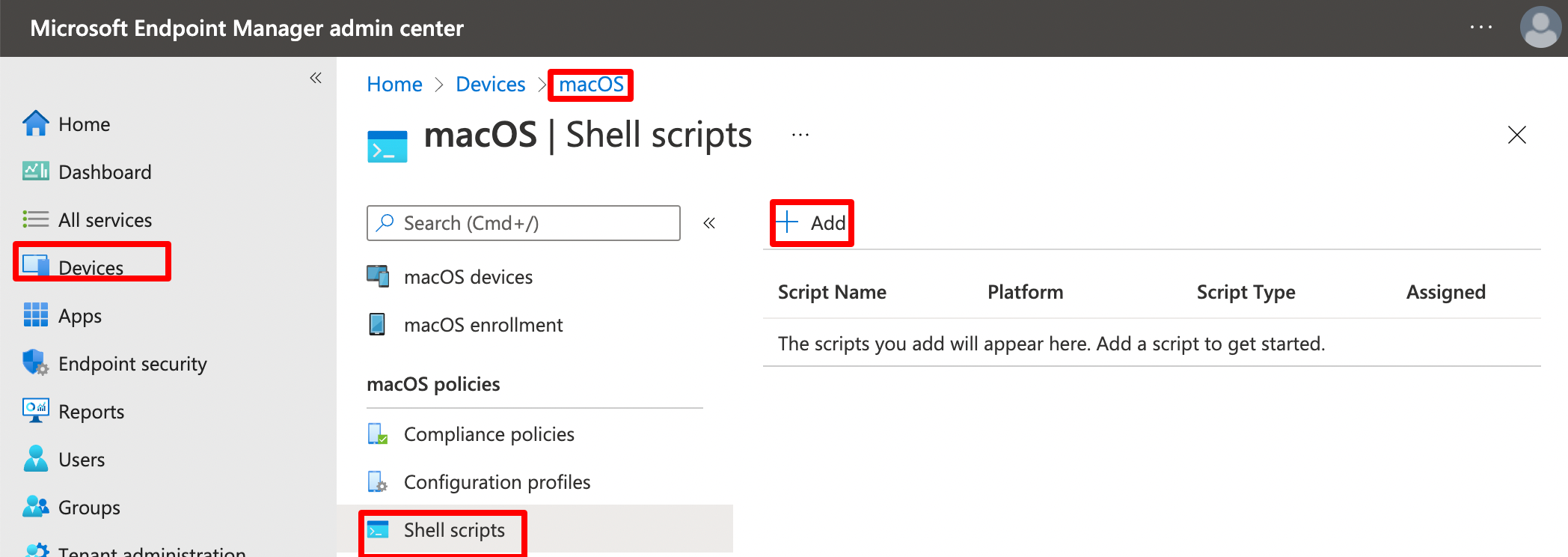
Once you have the script ready, deploy it to our macOS devices using Intune.
Go to Devices > macOS > Shell scripts > + Add
Give it a proper name, upload your script and configure as shown on the screenshot.
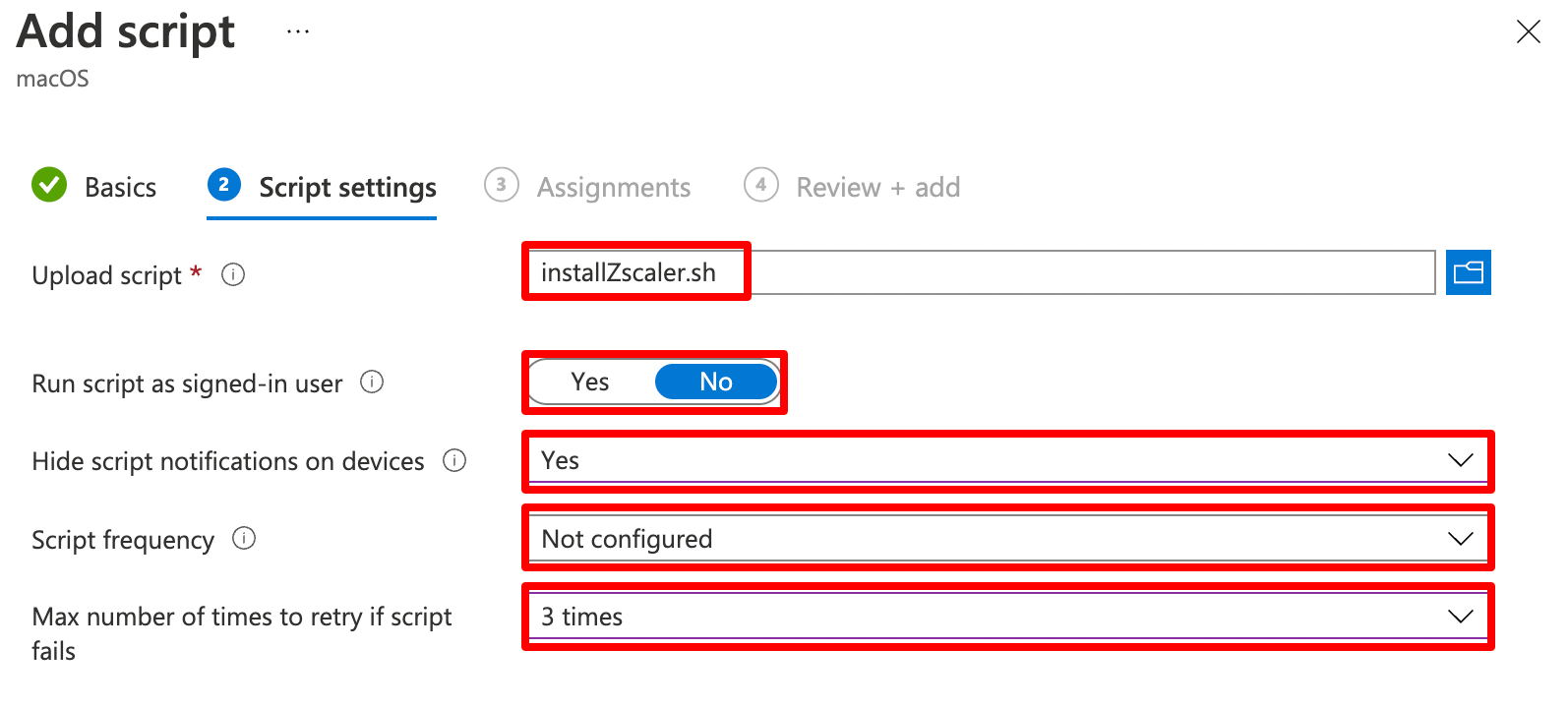
| Setting | Value | Description |
|---|---|---|
Run script as signed in user |
No | Script will run as root |
Hide script user notifications on devices |
Yes | No need to |
Script frequency |
Not configured | Will only run once. If you want to handle updates, you need to change this |
Maximum number of times to retry if script failes |
3 | Just in case |
Assign the script to the User Group
If your want to dive deeper, I recommend this article Deploying macOS apps with the Intune scripting agent. It also provides info how to obtain logs remotely in case you need to troubleshoot.
Enable Microsoft Enterprise SSO plugin
We have a username, but what about passwords? To achieve this we need to enable the Microsoft Enterprise SSO plugin for Apple devices.
The Microsoft Enterprise SSO plug-in for Apple devices provides single sign-on (SSO) for Azure Active Directory (Azure AD) accounts on macOS, iOS, and iPadOS across all applications that support Apple’s enterprise single sign-on feature.
This extension enables you to SSO into Zscaler App. No password required. The only requirement is that you use the Company Portal App. It is currently in public preview, so it’s officially not production ready, but works great. More details can be found on docs.microsoft.com. This extension also helps you if you have timeout policies in ZPA and need silent reauthentication.
Create a new configuration profile: Devices > macOS > Configuration Profiles > Create Profile > Select Profile Type Template > Device Features, give it a proper name.
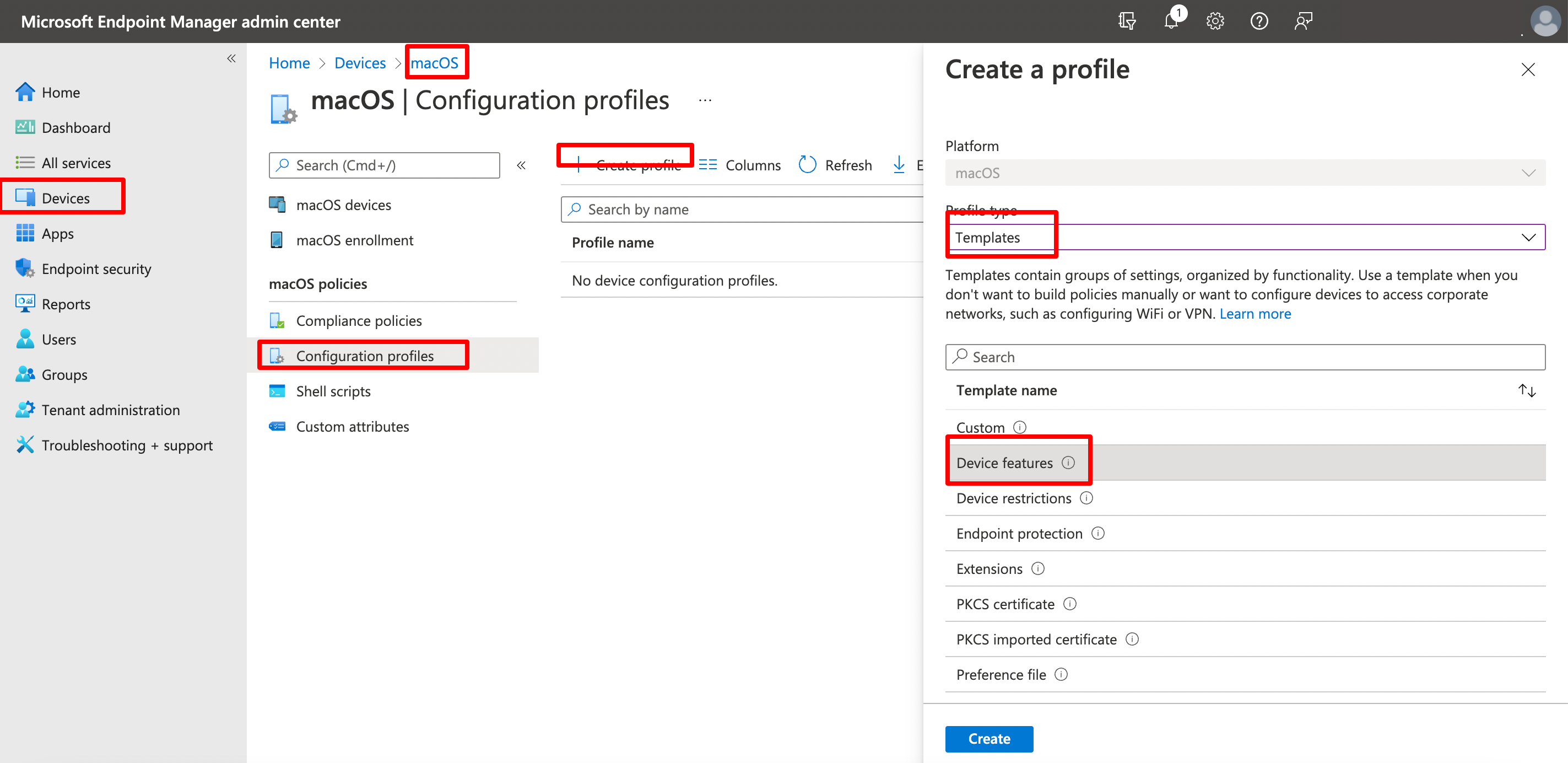
We need to configure settings as per below screenshot
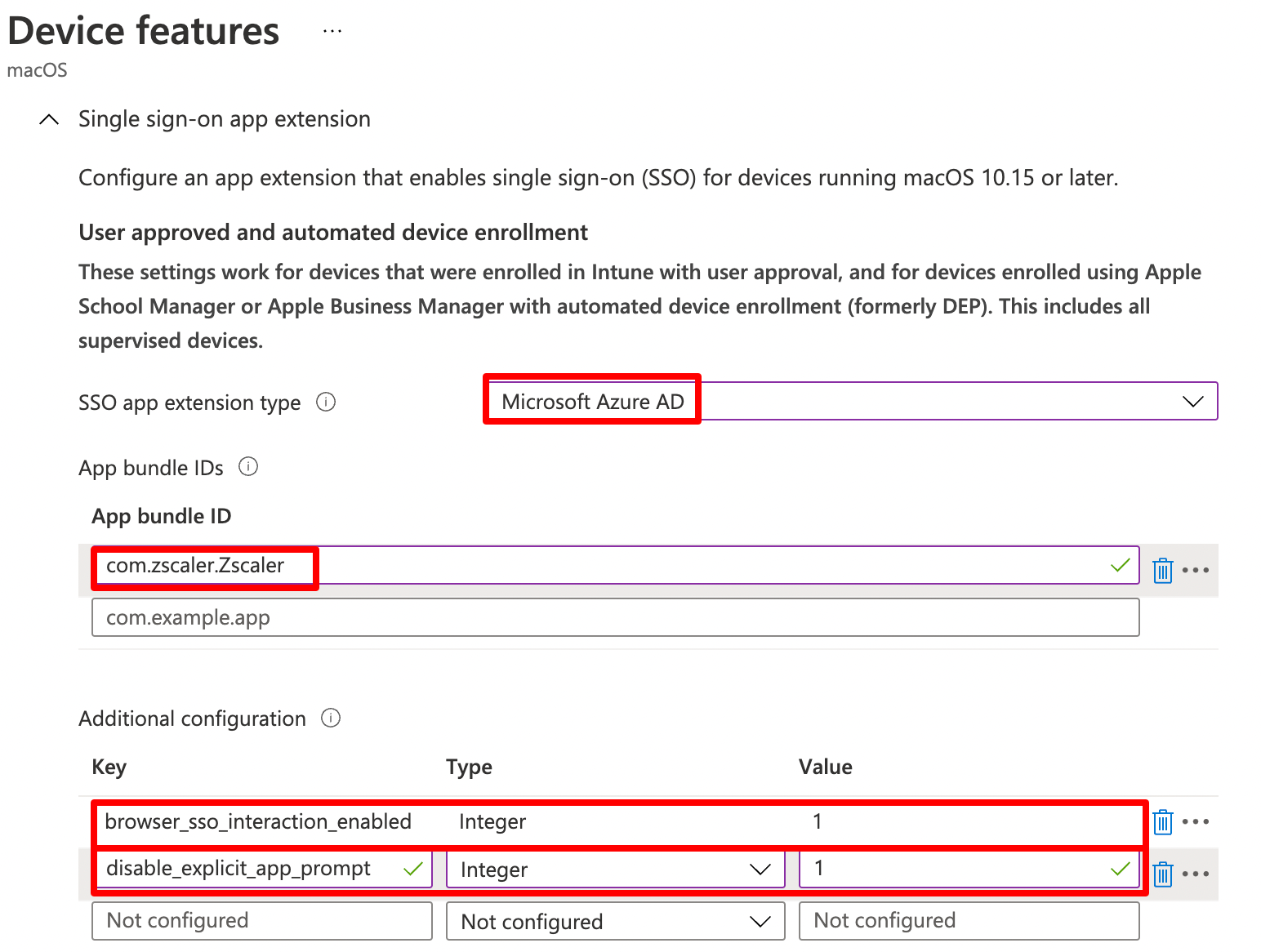
| Setting | Value |
|---|---|
SSO App Extension |
Microsoft Azure AD |
Enable shared device mode |
Not configured |
App Bundle ID |
com.zscaler.Zscaler (Make sure you have the last capital Z) |
We can also configure two additional configuration keys that are recommended by Microsoft
| Key | Type | Value | Description |
|---|---|---|---|
browser_sso_interaction_enabled |
Integer | 1 | Allow users to sign in from unknown applications and the Safari browser |
disable_explicit_app_prompt |
Integer | 1 | Disable OAuth 2 application prompts |
Assign the policy to the user group. That’s it.
Check in device
Now go to the company portal an check in the device. Zscaler should install automatically. To check SSO you can open the app, while it’s white in the tray. Should look something like this.
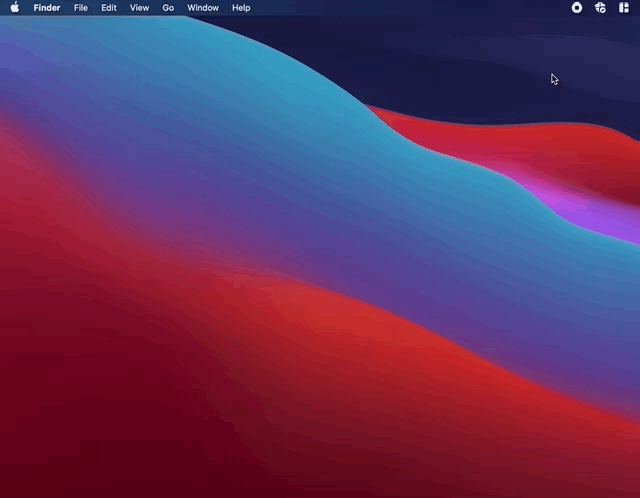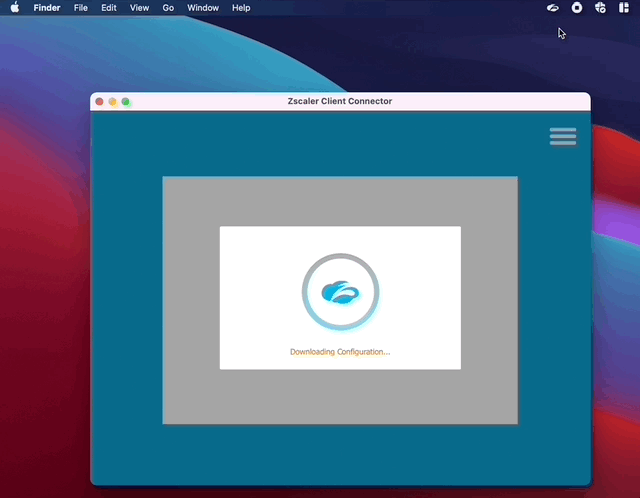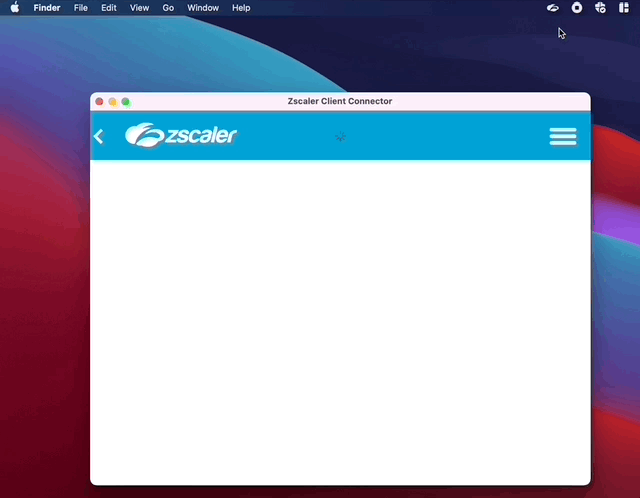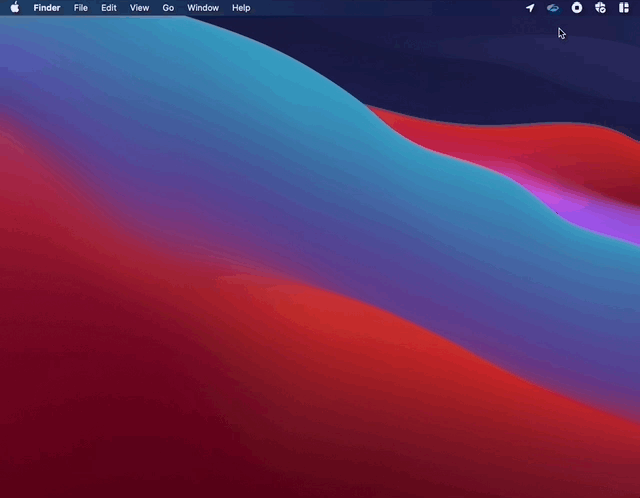
You may want to check the logfiles in /Library/Logs/Microsoft/Intune/ run tail -f *IntuneDaemon current*.log to see the progress.
Why can’t I install a real app?
Well you can. There is a great article in the Zscaler Community by Nathan Catania about how to do that. From my point of view the proposed method has some tradeoffs.
- You need an Apple Developer Account
- If you don’t have one, it can take some time until it’s activated, it’s 100$ a year
- You need to notarize the App and every version you deploy
- You need to notarize it for every authentication domain you have
Done
I hope you found this post useful. If you have questions or feedback, the best option to reach me is Twitter