Deploy Zscaler Client Connector to iOS with Intune

This is the first of four posts where I will describe how to deploy Zscaler Client Connector (aka the app) to the different OS platforms Zscaler and Intune support. The goal is to deploy the app and prepopulate all required information to the app to create as little user friction as possible. I start with iOS. This is what it will look like.

To achieve this, we need to configure a few things
- Push Zscaler Root Certificate to iPhone
- Create VPN Profile
- Add App in Intune
- Create App Configuration Profile
- Enable Azure AD SSO extension for Zscaler Client Connector
- Install App on iPhone
How To
First of all create a user group that
- is assigned to ZIA / ZPA enterprise applications in Azure AD
- has an Intune license
- can install the company portal on iOS and enroll their device
Let’s go!
Push Zscaler Root Certificate to iPhone
The SSL certificate is required if you use SSL inspection (which I definitely recommend). Even if you don’t use it on iOS in first place it’s good to have it on the device . We will deploy the Zscaler root certificate. In your ZIA Portal go to Policy > SSL Inspection > Advanced SSL Inspection Settings and download the Zscaler Certificates.

Unzip the file and create a new configuration profile in Intune. Click Devices > iOS/iPadOS > Configuration Profiles > Create Profile > Select Profile Type Template > Trusted Certificate. Upload the previously downloaded certificate. Assign the certificate to the user group!

It will appear in your iOS Certificate Store in Settings > General > About > Certificate Trust Settings once the device checked in to Intune.
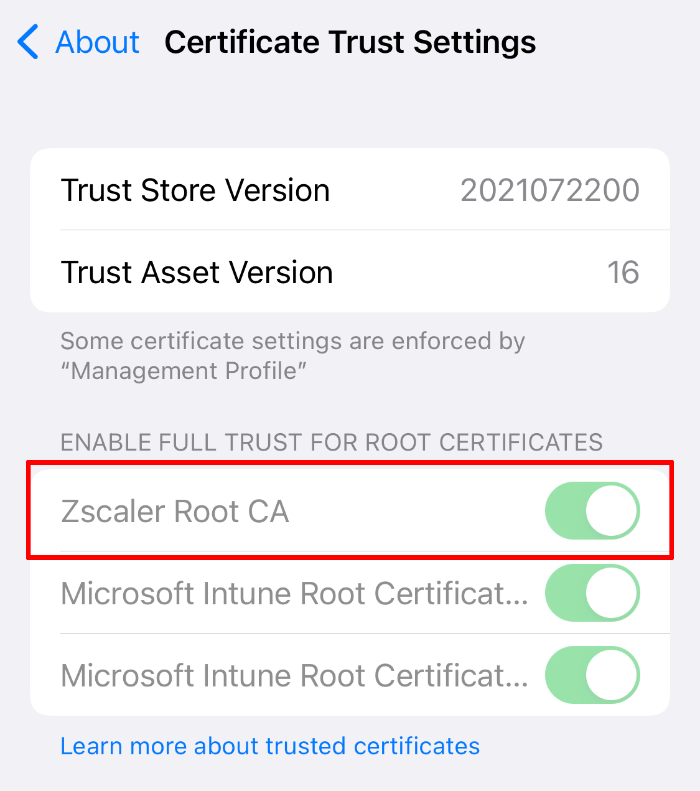
Create VPN Profile
The VPN profile we’re going to deploy is not a real VPN profile. It redirects web traffic into the app. If you don’t push it to the phone it will be created during first sign on of the app, requesting the user to enter the device Passcode.
To create the profile go to Devices > iOS/iPadOS > Configuration Profiles > Create Profile > Select Profile Type Template > VPN

In configuration settings you need to configure:
| Setting | Value |
|---|---|
Connection Type |
Zscaler |
Connection Name |
Up to you |
Custom domain name |
Domain name you use for authentication. Different UPN suffixes require different VPN Profiles. |
Strict Enforcement |
Not configured. Requires supervised devices |
Organization's cloud name |
The name of you ZIA cloud without tld. zscaler.net = zscaler zscloud.net = zscloud |
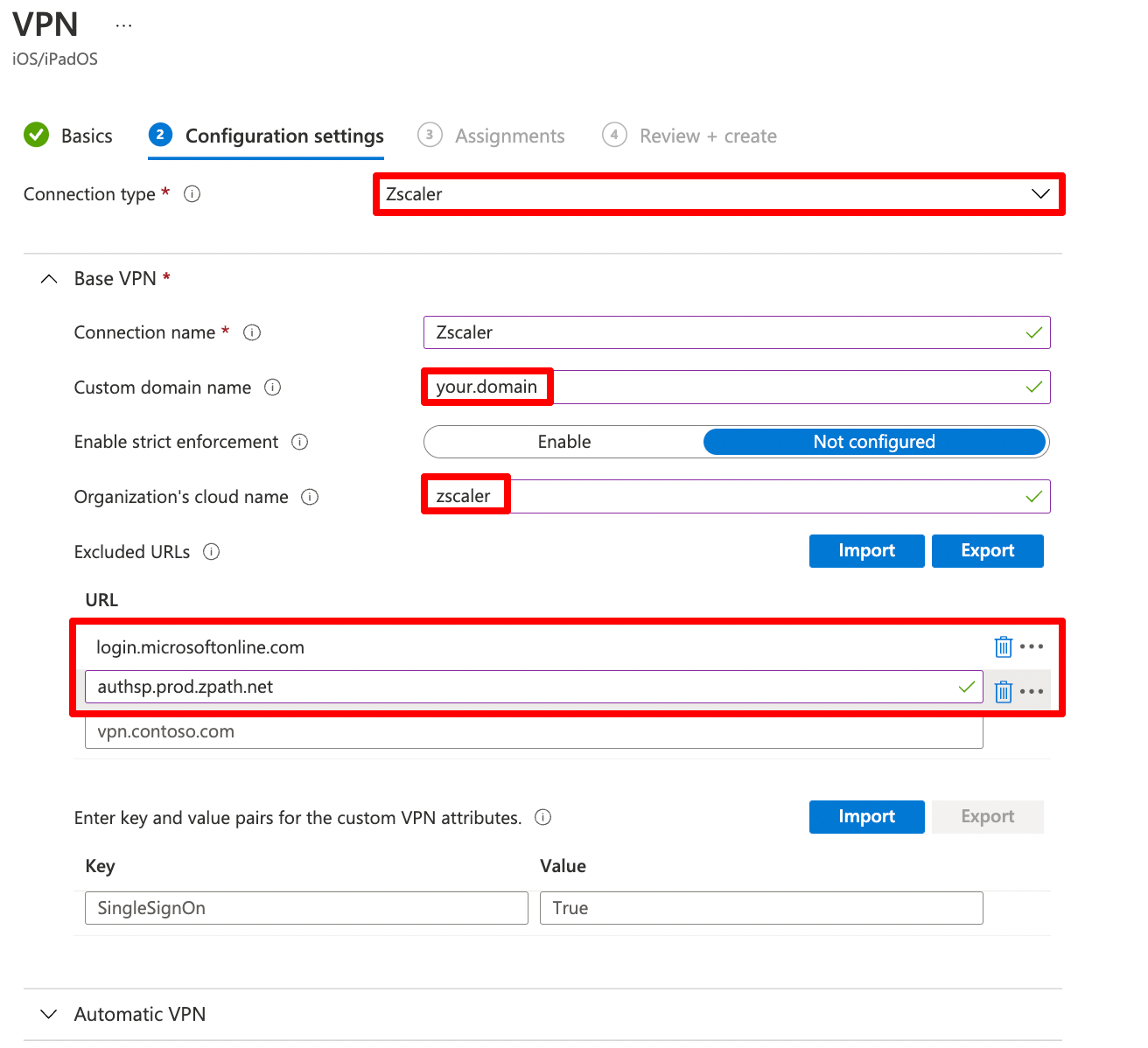
The exlcuded URLs login.microsoftonline.com and authsp.prod.zpath.net are only required if you use strict enforcement. Strict enforcment enforces all traffic to go through Zscaler. It requires supervision.
Assign the VPN to the user group.
Add App in Intune
Next we need to add the App in Intune. Go to Apps > iOS/iPadOS > + Add > Select iOS Store App and click Select
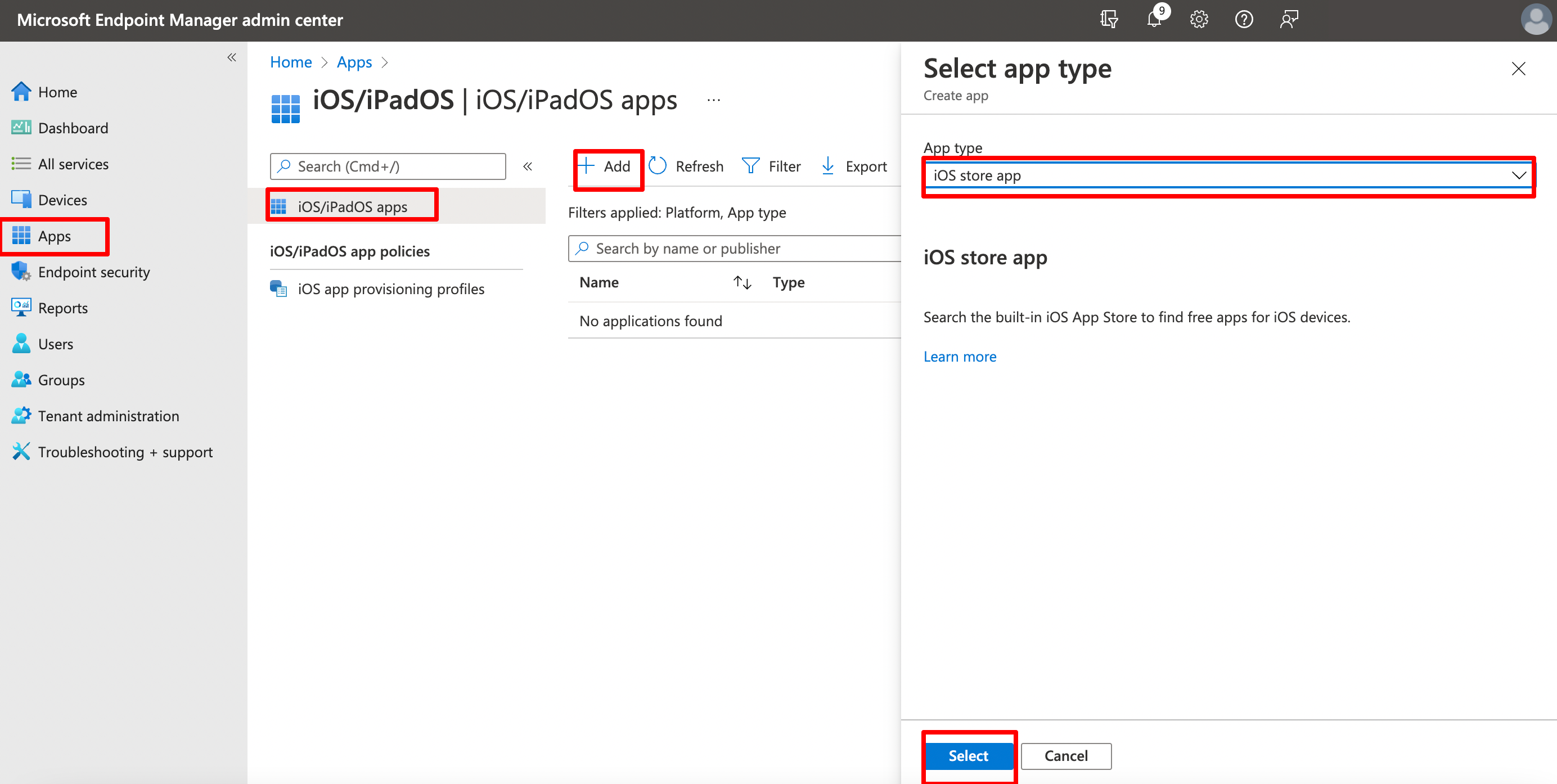
On the next page click Search App Store and search for Zscaler. Select Zscaler Client Connector.

On the next pages no modifications are required. You may want to set it as featured. Assign the app as required to the user group. This will prompt the user to install the app automatically on the device. If you want the app to be enforced on the dvice you will need supervised mode.
Create App Configuration Policy
Next we need to give the app some information about the Zscaler service it should connect to. In iOS this is done through an App Configuration Policy.
Go to Apps > App Configuration Profiles > + Add > Managed Devices
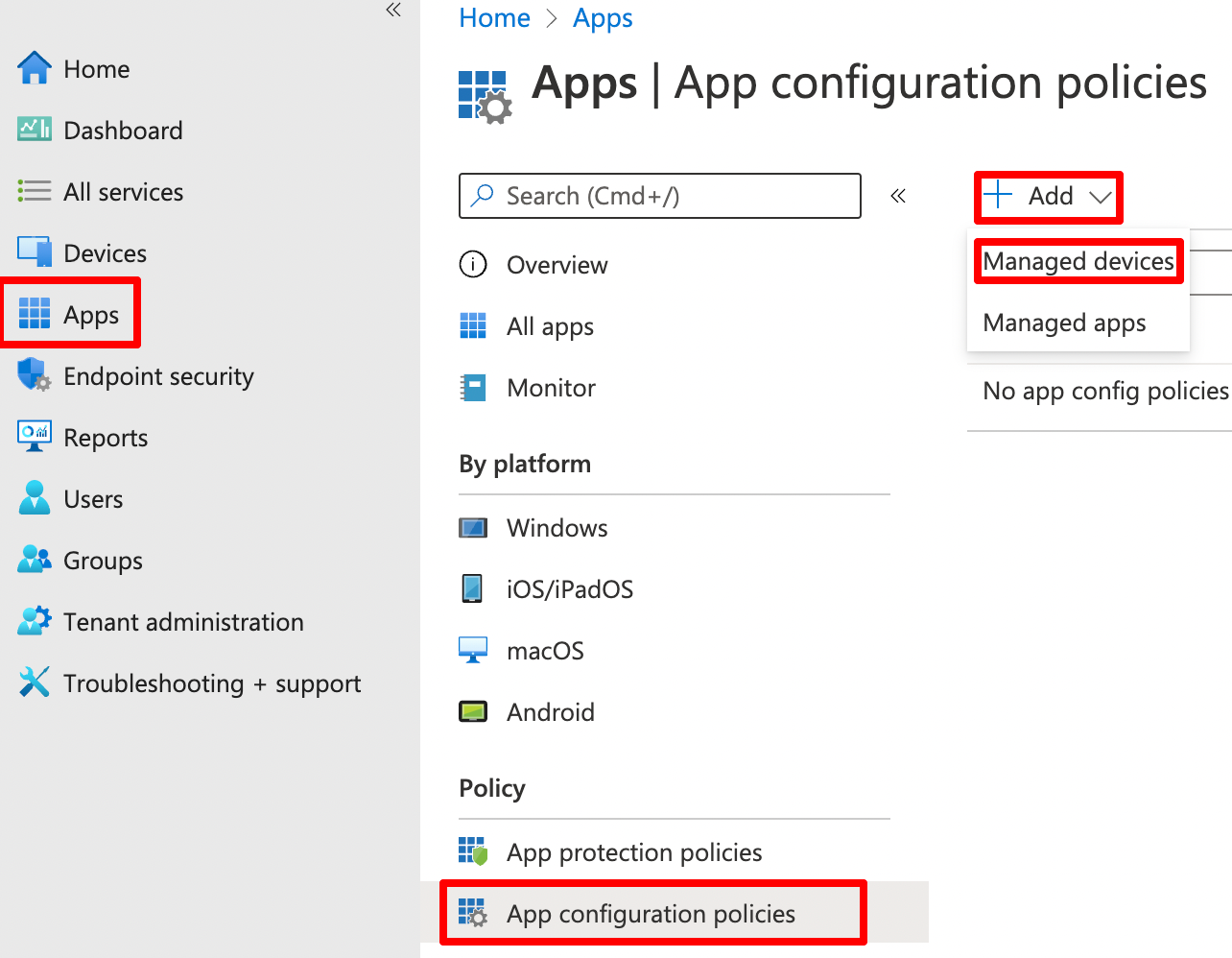
On the Basic page we need to configure below settings. Please note that the Zscaler Client connector will only appear, if you already assigned it in Intune.
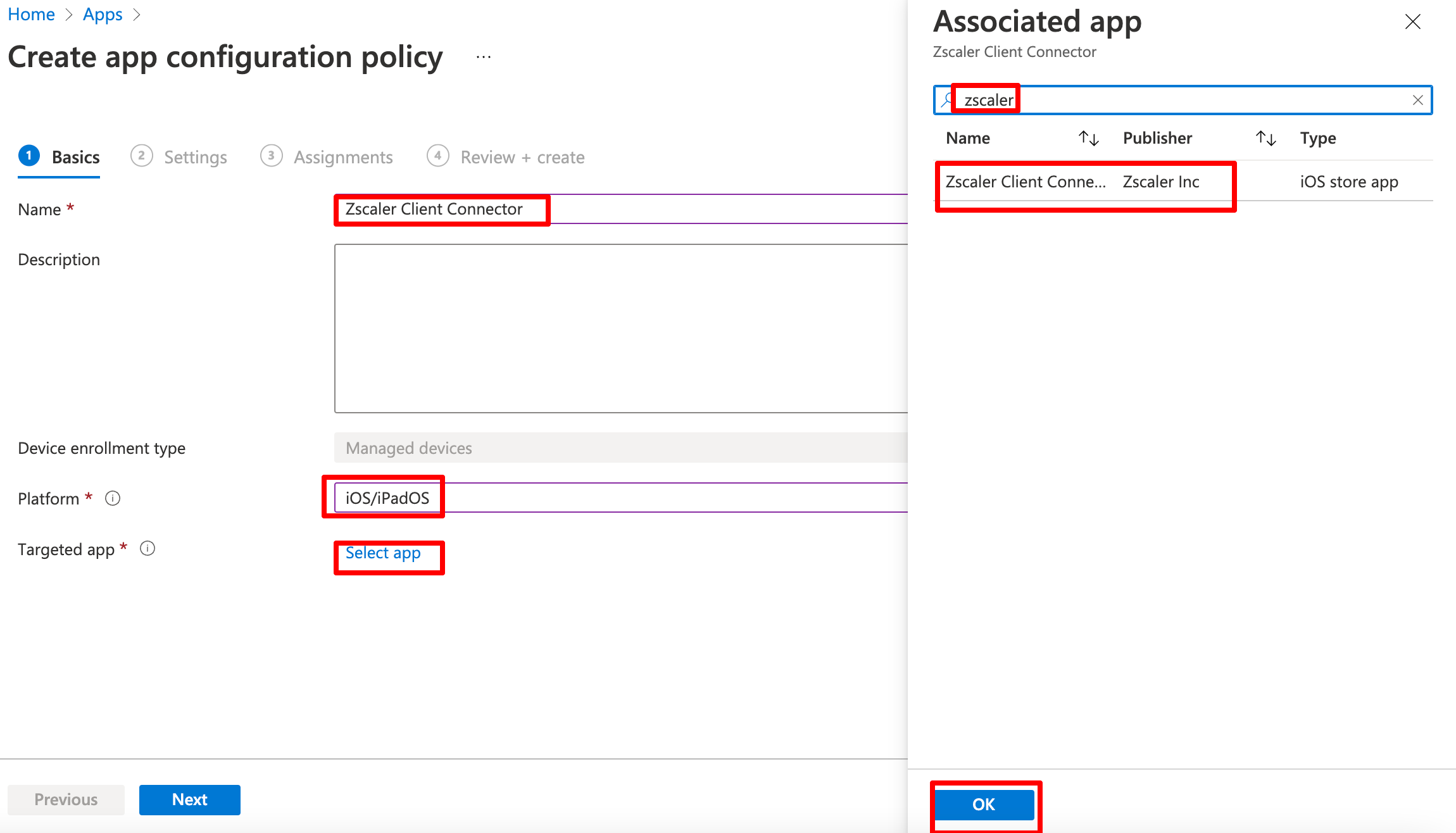
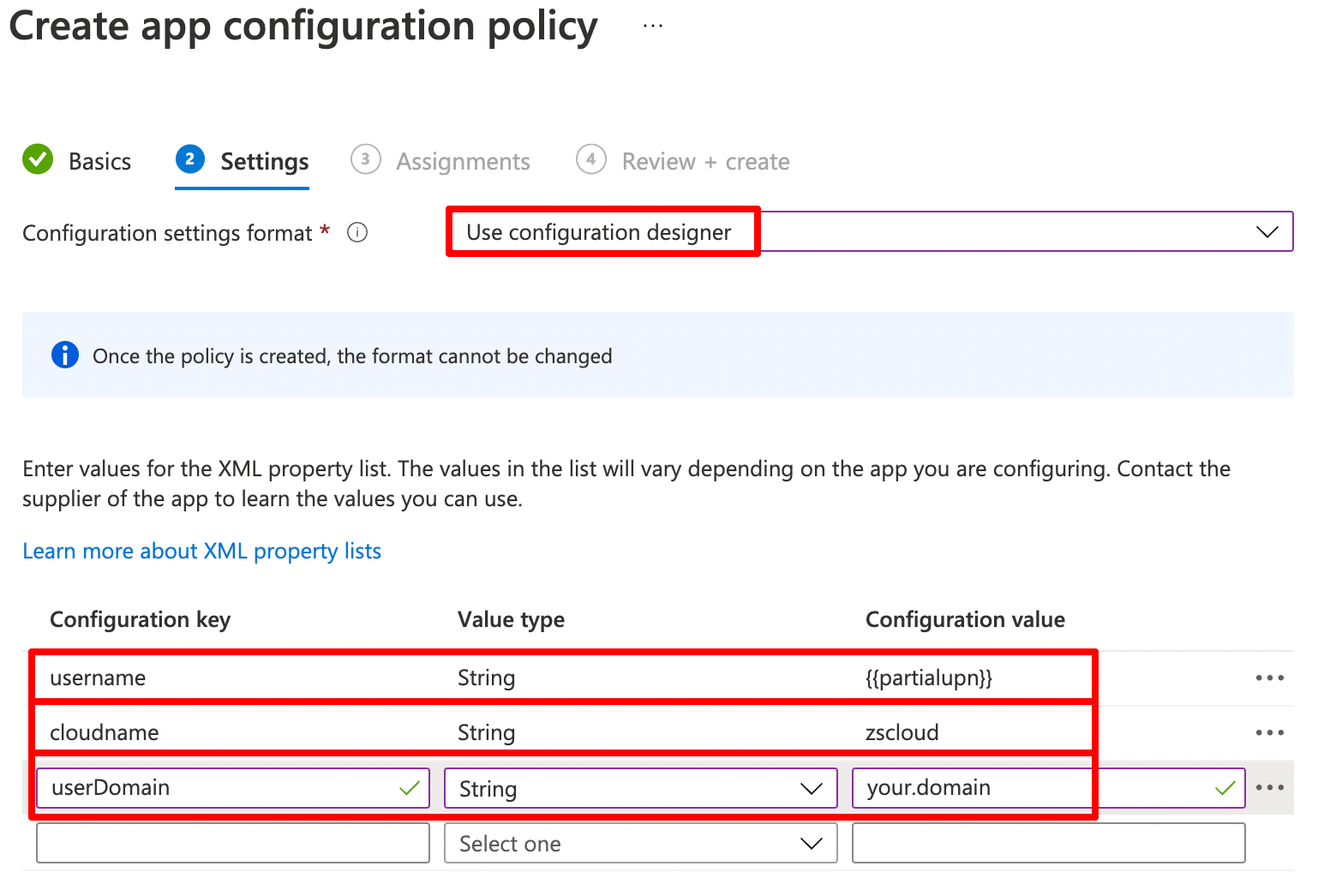
Now we can configure the app settings. Select Use configuration designer. A basic installation require three properties. Please note: they are case sensitive.
| Setting | Value | Description |
|---|---|---|
username |
{{partialupn}} | This is the part before the @ in your username. |
cloudname |
e.g. zscloud | The name of you ZIA cloud without tld. zscaler.net = zscaler zscloud.net = zscloud |
userDomain |
your.domain | Domain name you use for authentication. |
Zscaler builds the username to login using {{partialupn}}@userDomain. Click next and assign the policy to the user group.
Assign the policy to the user group.
Enable Microsoft Enterprise SSO plugin for Zscaler Client Connector
Well now we have a username, but what about passwords? To achieve this we need to enable the Microsoft Enterprise SSO plugin for Apple devices.
The Microsoft Enterprise SSO plug-in for Apple devices provides single sign-on (SSO) for Azure Active Directory (Azure AD) accounts on macOS, iOS, and iPadOS across all applications that support Apple’s enterprise single sign-on feature.
This extension enables you to SSO into Zscaler App. No password required. The only requirement is that you use Microsoft authenticator. It is currently in public preview, so it’s officially not production ready, but works great. More details can be found on docs.microsoft.com. This extension also helps you if you have timeout policies in ZPA and need silent reauthentication.
Create a new configuration profile at Devices > iOS/iPadOS > Configuration Profiles > Create Profile > Select Profile Type Template > Device Features, give it a proper name.
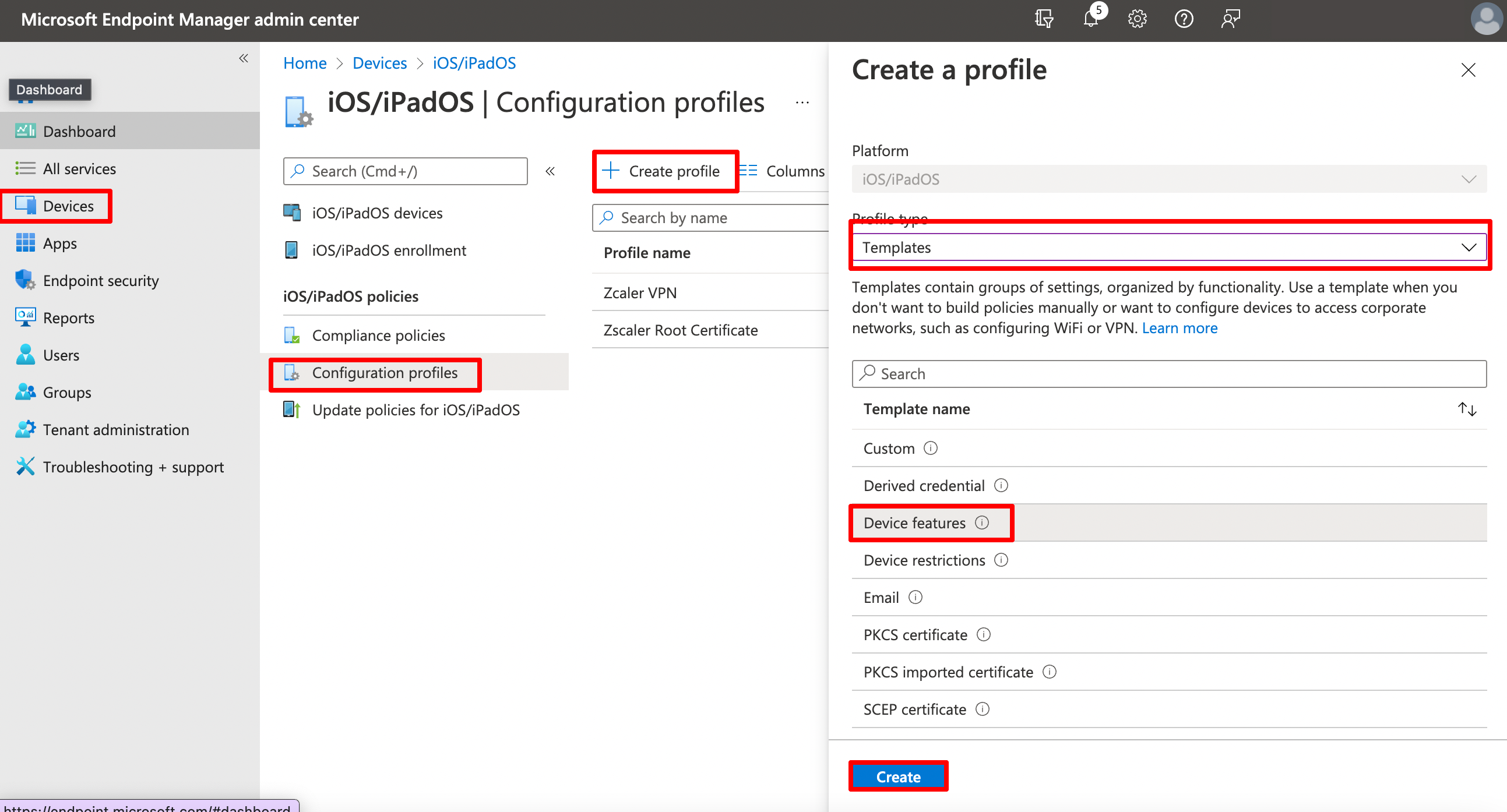
On the next page we will configure the Single sing-on app extension.
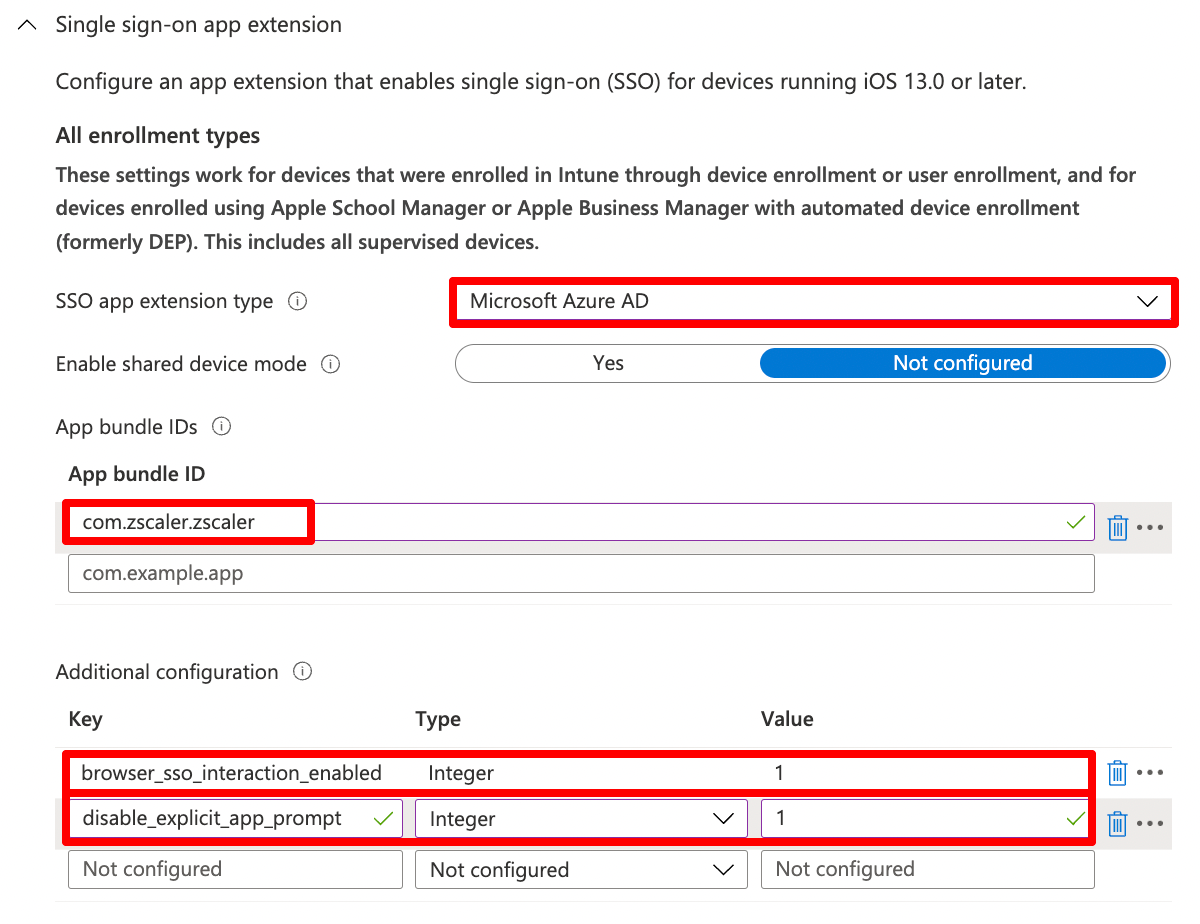
We need to configure
| Setting | Value |
|---|---|
SSO App Extension |
Microsoft Azure AD |
Enable shared device mode |
Not configured |
App Bundle ID |
com.zscaler.zscaler |
We also configure two additional configuration keys that are recommended by Microsoft
| Key | Type | Value | Description |
|---|---|---|---|
browser_sso_interaction_enabled |
Integer | 1 | Allow users to sign in from unknown applications and the Safari browser |
disable_explicit_app_prompt |
Integer | 1 | Disable OAuth 2 application prompts |
Assign the configuration profile to the user group.
If it’s deployed correctly, it should appear in your intune management profile.
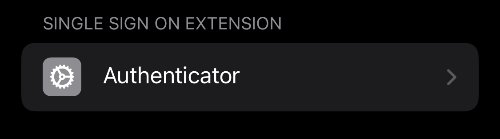
Install app on iPhone
That’s it. Now you can go to your company portal and checkin your device. You should see certificaze, vpn profile, ann sso extension in your management profile. Install the app.
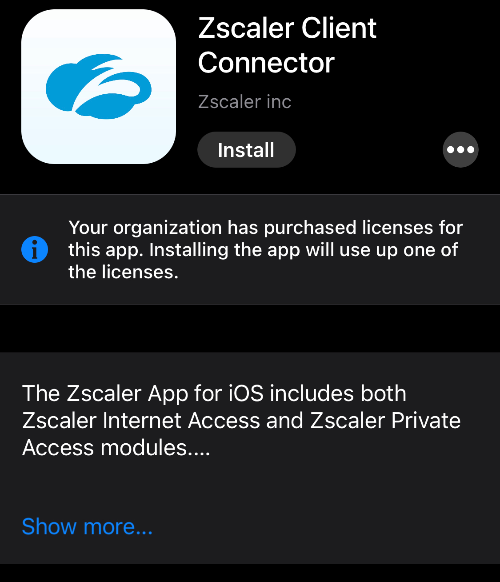
Zscaler should now automatically sign in once you open it.
Done
I hope you found this post useful. If you have questions or feedback, the best option to reach me is Twitter
Appreciations
This article is standing on the shoulders of this post in the Zscaler Community by Nathan Catania. It is outlines all the options you need to configure supervised devices, deviceTokens etc.
I also would like point to Peter van der Woude’s blog. It’s a greate resrouce for MEM topics. I used his articles on Partial UPN and SSO Extension